是的,我们又是冠军
-
2025年终总结
小总结 X 照片分享 √
-
强网杯-2025
又被带飞了
-
华为杯-2025
不好评价,办的一坨屎
-
强网拟态-2025
我们是 冠军!
-
羊城杯-2025-初赛
一血拿拿拿
-
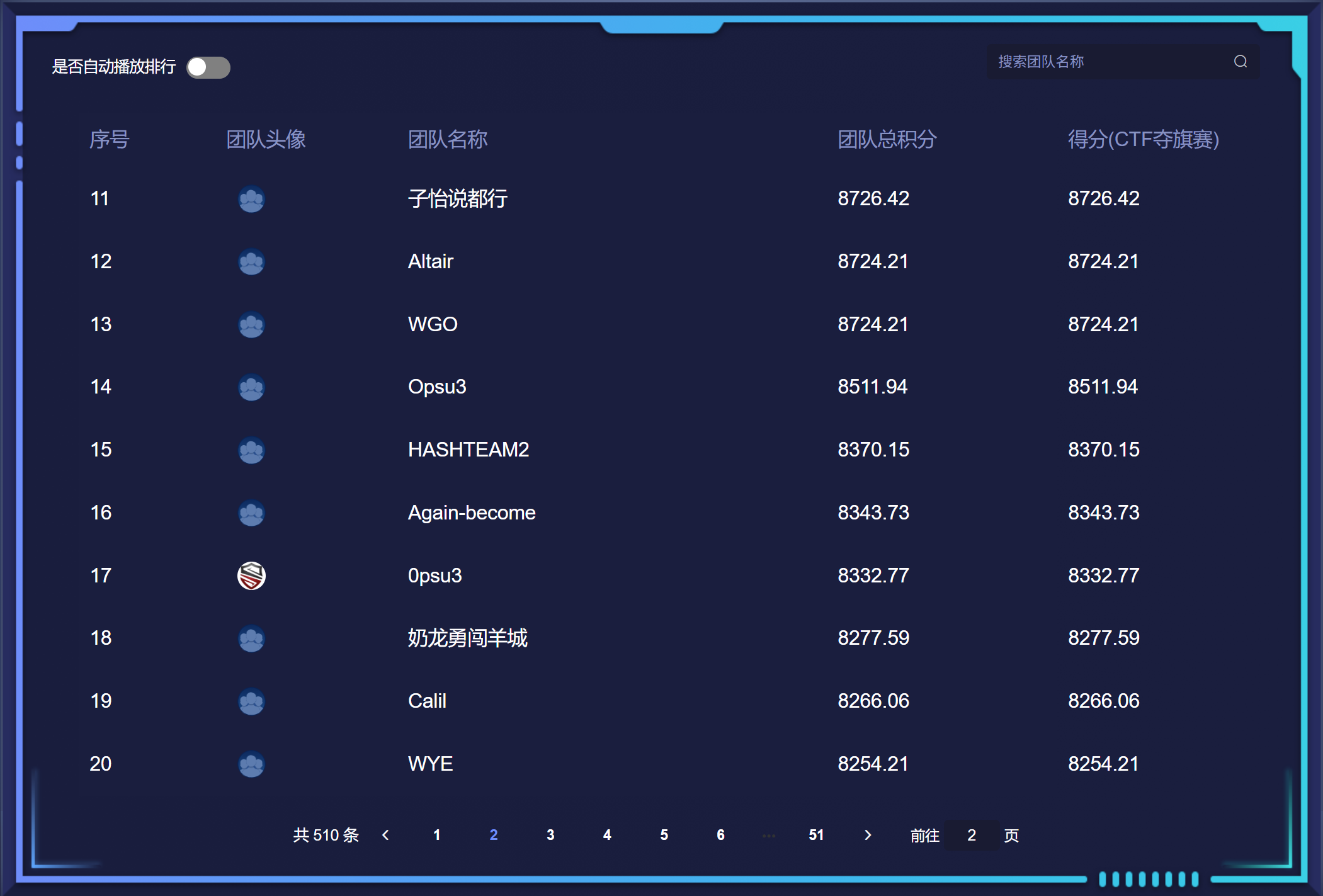
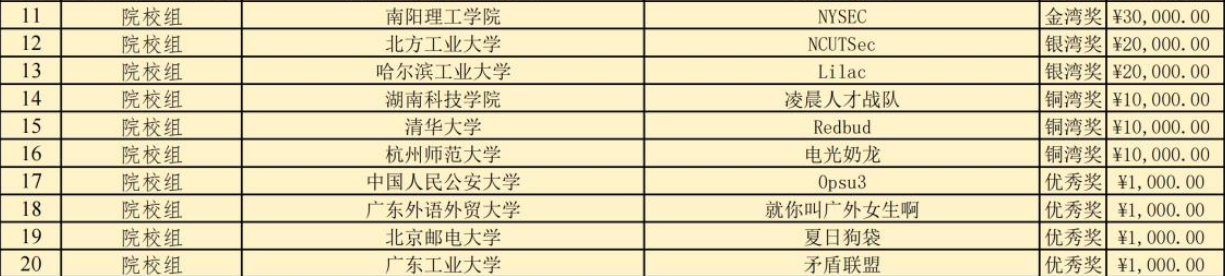
湾区杯-2025
洋参还没发力,发力已经+1w了
-
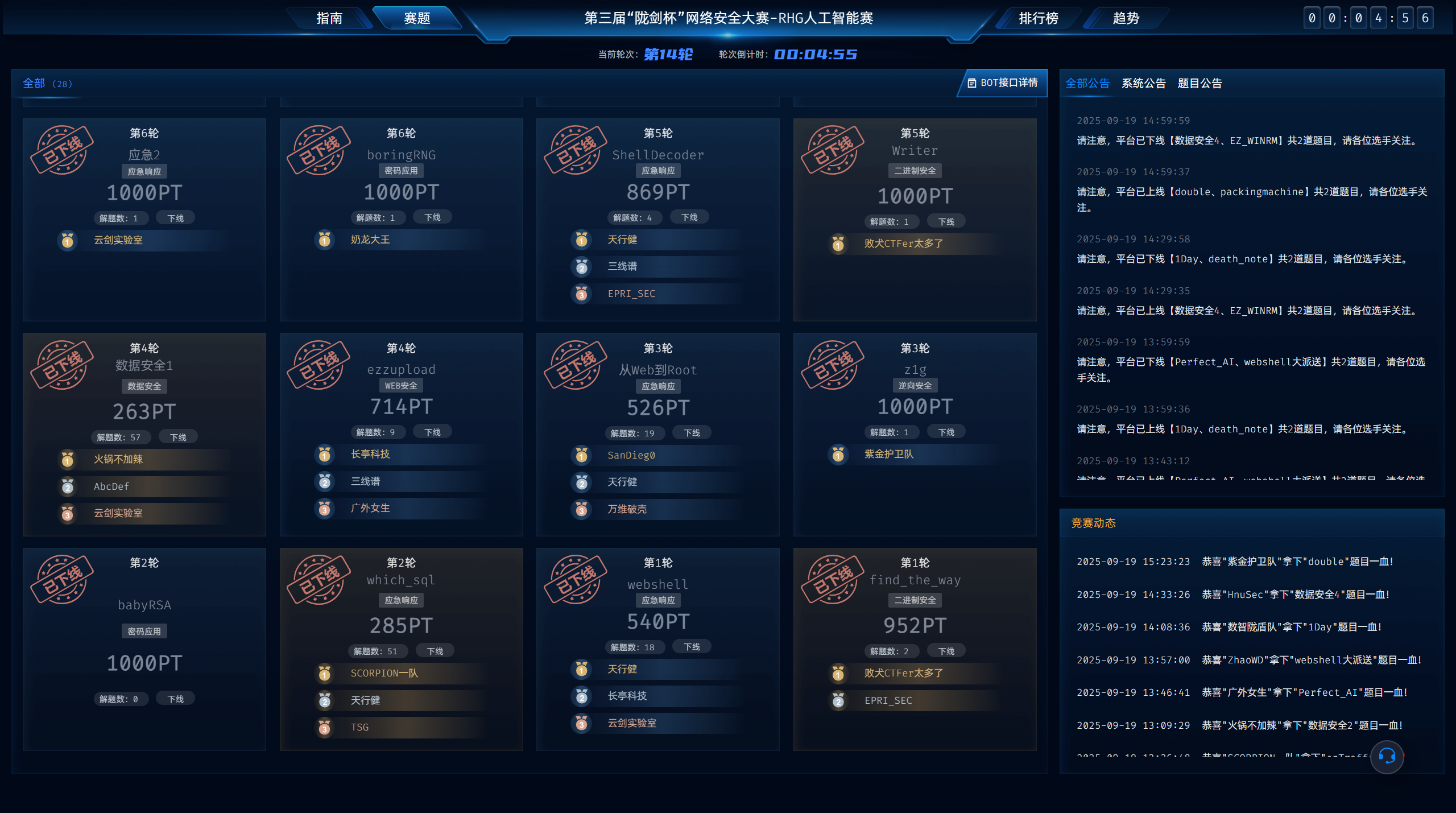
陇剑杯-2025
差4分钟做出easypivot,差4分钟做出easyupload
-
DK盾-CTFers赞助计划已启动!
dk盾!
-
ciscn-2025-决赛
有惊无险