hkcertctf-2025
HKcertCTF 2025 WP
a_strange_rop
负数溢出越界写,rop直接getshell
1 | #!/usr/bin/env python3 |
piano
1 | diff --git a/quickjs.c b/quickjs.c |
将sp–操作移到了外面,在JS_SetPropertyInternal抛出异常时,不会执行sp–,导致uaf
uaf原语
1 | Object.defineProperty(globalThis, "x", { |
利用思路是通过uaf可以任意伪造JSObject,但是最开始没有地址,所以选择伪造 JSString,越界读来获得地址
拿到地址后,直接伪造JSArrayBuffer即可任意读写
1 | Object.defineProperty(globalThis, "x", { |
tips:
这题的断点调试可以将断点打在write,利用console.log来当断点
stop
ret2syscall srop
1 | #!/usr/bin/env python3 |
nofile
fmt dump下来elf,然后打got改成后门
exp from qanux
1 | from pwn import * |
filesystem
filesystem revenge
使用""绕过,"f""lag"==flag
compress
先利用show泄露地址,负数溢出越界写,写stdin结构体,打musl的iofile,利用gadget来rop
1 | #!/usr/bin/env python3 |
link start!
在选择method有负数溢出,将其改成got[1],然后触发hidden method即可秒杀
1 | #!/usr/bin/env python3 |
childcode
利用imul清空寄存器
dec eax控制rax
xchg dword ptr fs:[rcx], eax``xchg dword ptr fs:[rbp], edi控制rdi
cmovno是条件mov,可以直接用来充当mov
思路是先用shmget``shmat来分配一段rw地址作为栈和bss
然后openat``readv``writevorw
这是GPT5 pro思考一个半小时出的
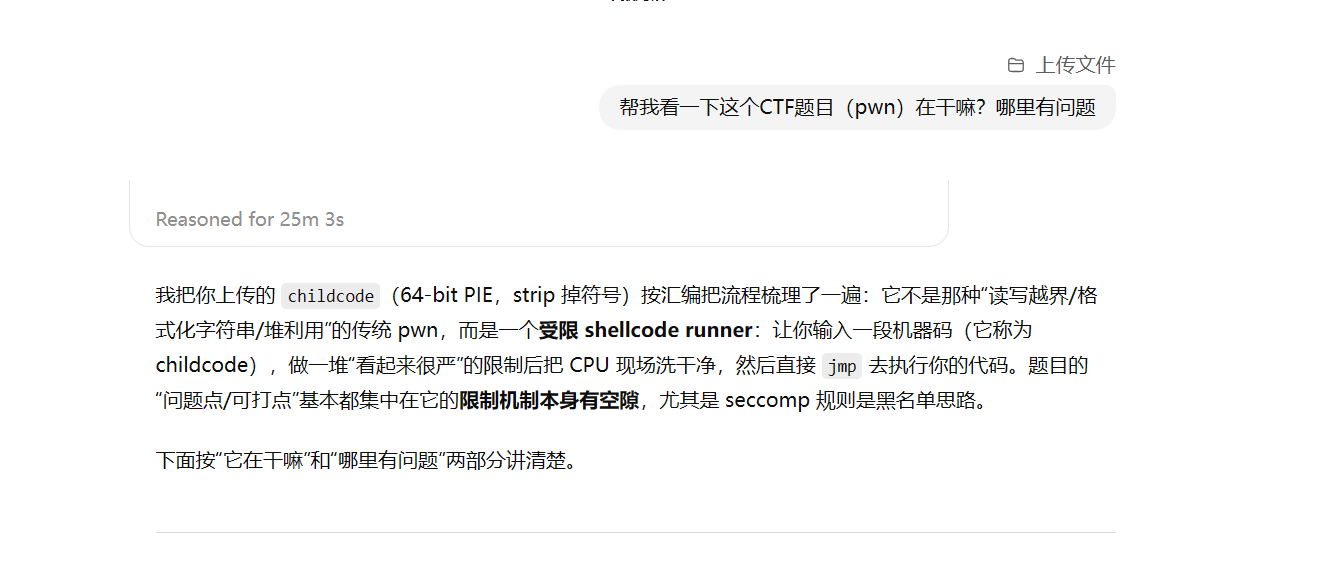
仅需两句提示词
1 | imul edi, edi, 0 |
RANK
- 标题: hkcertctf-2025
- 作者: InkeyP
- 创建于 : 2025-12-22 09:03:56
- 更新于 : 2025-12-22 09:30:45
- 链接: https://blog.inkey.top/202512/22/hkcertctf-2025/
- 版权声明: 本文章采用 CC BY-NC-SA 4.0 进行许可。
评论